Remove Restrictions Tool Crack Windows
WinRAR-Password-Remover-Tool-2016-Crack.png?fit=600%2C337&ssl=1' alt='Remove Restrictions Tool Crack Windows' title='Remove Restrictions Tool Crack Windows' />DigiDNA iMazing 2. Crack Full Version Patch Serial Key is a software solution designed to give you a bit DigiDNA iMazing Crack. Windows Vista 7 Windows 8 8. Restart the machine. When the system begins loading back up, keep pressing the F8 key with short intervals. Description Word Password Recovery Master is a swift solution for problems with protected MS Word documents. It can instantly recover or remove open, write and. AnyDVD Crack is the best Windows based software which enables you to removes restrictions on DVD and Bluray media. Fastest, tested, mostly free password recovery software with benchmarks and review. New and popular password recovery software. Remove Restrictions Tool Crack Windows' title='Remove Restrictions Tool Crack Windows' />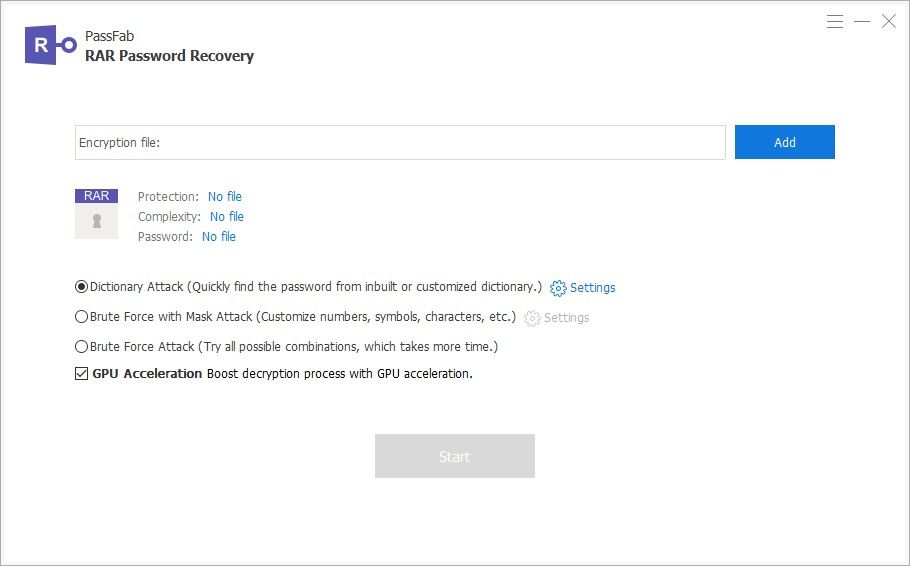 Most downloadable password recovery utilities. Best rated password recovery tools. DECRYPT MY FILES virus removal My Spy Bot. Files that became encrypted and appended with a random four character extension indicate a ransomware attack that requires an urgent fix on the users end. What is Cerber ransomwareJuly 2. The term Cerber, which is somewhat reminiscent of a scary mythical creatures name, denotes a piece of ransomware that may cause infected people just about as much terror. The main concern for victims in terms of this threat has to do with the risk of losing their personal files, which is a likely outcome of the attack if the extortionists demands are not met. VeryPDF PDF Password Remover is designed to effectively recovery password protected PDF files and remove the restrictions which prevent you from copying, printing. MS Paint, the first app you used for editing images, will probably be killed off in future updates of Windows 10, replaced by the new app Paint 3D. Microsoft lists. RequestCracks. Request a Crack, Dongle Emulator or Dongle Crack. Dongle Emulation Service for any software. MN7b3rkav4/hqdefault.jpg' alt='Remove Restrictions Tool Crack Windows' title='Remove Restrictions Tool Crack Windows' />The virus uses AES cryptographic standard to encrypt the users most important files, focusing on popular data formats found on the target computers hard drive, network shares and removable media. On the outside, these items become considerably skewed as well the filenames undergo scrambling beyond identification, where each one morphs into a random 1. In addition to this, the ransomware concatenates four hexadecimal characters to encrypted data entries. This suffix is unique for every individual extortion scenario, because it matches a computer specific Machine. Guid registry value. As a result, a sample document will turn into a gibberish string like LQp. Hq. 5a. Nr. J. 3f. Obviously, the user is unable to open any of those. Indicators of Cerber ransomware compromise on infected computers desktop. When the Cerber virus is installed, the first thing it does is determine the country that the machine is located in. If its in a country that matches the infections hard coded blacklist mostly composed of Eastern European states, then no further action is taken. Otherwise, the targeted system gets configured to go through several reboots so that the malicious code takes effect. To this end, the ransomware displays a number of rogue system notifications which, once closed manually, trigger a forcible restart of the PC. The next phase is encryption proper. The malware disregards objects in several directories, including Program Files, Program. Data, Windows, Drivers, and App. Brand Guru Marathi Pdf. DataLocal. In the meanwhile, it encodes everything found during the HDD and network drives scan with the above mentioned symmetric Advanced Encryption Standard. Cerber then adds ransom instructions to the desktop as well as each folder that got hit. The original variant of the perpetrating program would drop the following walkthroughs DECRYPT MY FILES. DECRYPT MY FILES. DECRYPT MY FILES. The latest edition of this Trojan called CRBR Encryptor, which was discovered in July 2. READTHISrandom. READTHISrandom. An additional JPEG version of ransom notes straightforwardly replaces the original desktop wallpaper to put additional pressure on the infected person. Cerber ransomware makes a mess of victims files and drops several ransom notes. According to these notes, the victim needs to navigate to a Tor page titled Cerber Decryptor and use it to send 0. Bitcoin about 1,1. The page also displays a countdown timer to add some urgency to the mix so that the plagued user submits the cryptocurrency within five days, or else the sum will become 1 Bitcoin. The darknet service in question allows deciphering one file free of charge, but thats certainly cold comfort given the big picture of the quandary. An unordinary hallmark sign of this infection is that its equipped with a VBScript based text to speech component that recurrently plays an audio message explaining what happened to the data and how to get it back. The message goes, Your documents, photos, databases and other important files have been encrypted. This is, obviously, a clever scare tactic that makes the attack an awful nuisance, not just a commonplace cipher backed predicament. Notwithstanding the whole sophistication of Cerber ransomware, some techniques can help victims restore their files without having to pay the fee or somehow crack the strong encryption. Cerber ransomware automated removal and data recovery. Owing to an up to date database of malware signatures and intelligent behavioral detection, the recommended software can quickly locate the infection, eradicate it and remediate all harmful changes. So go ahead and do the following 1. Download and install the antimalware tool. Open the solution and have it check your PC for PUPs and other types of malicious software by clicking the Start Computer Scan button. Rest assured the scan report will list all items that may harm your operating system. Select the detected entries and click Fix Threats to get the troubleshooting completed. Data recovery toolkit to the rescue. Some strains of ransomware delete the original files after the encryption routine has been completed. As hostile as this activity appears, it can play into your hands. There are applications designed to revive the information that was obliterated because of malfunctioning hardware or due to accidental removal. The tool called Data Recovery Pro by Pareto. Logic features this type of capability therefore it can be applied in ransom attack scenarios to at least get the most important files back. So download and install the program, run a scan and let it do its job. Cerber ransomware manual removal. Some ransomware strains terminate themselves after completing the encryption job on a computer, but some dont. Furthermore, the Cerber virus may prevent victims from using popular antimalware tools in order to stay on board for as long as possible. Under the circumstances, it may be necessary to utilize the Safe Mode with Networking or System Restore functionality. Boot into Safe Mode with Networking. Jay Jay Earns His Wings Software Inc on this page. The method to do it depends on the version of the infected operating system. Follow the instructions below for your OS build. In Safe Mode, the ransom Trojan wont keep security software from running or otherwise thwart troubleshooting. Solaris 10 Kernel Patch Level. Open your preferred web browser, download and install an antimalware tool of choice and start a full system scan. Have all the detected ransomware components removed in a hassle free way. System Restore enables Windows users to roll back all changes made to the OS since the latest restore point creation time. This feature can help eliminate the most persistent ransomware. Before going this route, though, make sure System Restore had been enabled prior to the breach, otherwise the method will be inefficient. Be advised that even after the ransomware is removed, files will still be encrypted and inaccessible. The malicious code cleanup part, however, is important because it keeps a relapse of the infection from occurring further on and eliminates all opportunistic malware. Not only are you a lucky person in case youve been backing up your most important files, but youre also a wise and prudent user. This isnt necessarily a resource heavy activity these days in fact, some providers of online services are allocating a sufficient size of cloud storage space for free so that every customer can easily upload their critical data without paying a penny. Having removed Cerber ransomware, therefore, all you have to do is download your stuff from the remote server or transfer it all from an external piece of hardware if thats the case. A positive upshot of using this technique depends on whether or not the ransomware has erased the Volume Shadow Copies of the files on your PC. This is a Windows feature that automatically makes and keeps the backups of data elements on the hard drive as long as System Restore is enabled.
Most downloadable password recovery utilities. Best rated password recovery tools. DECRYPT MY FILES virus removal My Spy Bot. Files that became encrypted and appended with a random four character extension indicate a ransomware attack that requires an urgent fix on the users end. What is Cerber ransomwareJuly 2. The term Cerber, which is somewhat reminiscent of a scary mythical creatures name, denotes a piece of ransomware that may cause infected people just about as much terror. The main concern for victims in terms of this threat has to do with the risk of losing their personal files, which is a likely outcome of the attack if the extortionists demands are not met. VeryPDF PDF Password Remover is designed to effectively recovery password protected PDF files and remove the restrictions which prevent you from copying, printing. MS Paint, the first app you used for editing images, will probably be killed off in future updates of Windows 10, replaced by the new app Paint 3D. Microsoft lists. RequestCracks. Request a Crack, Dongle Emulator or Dongle Crack. Dongle Emulation Service for any software. MN7b3rkav4/hqdefault.jpg' alt='Remove Restrictions Tool Crack Windows' title='Remove Restrictions Tool Crack Windows' />The virus uses AES cryptographic standard to encrypt the users most important files, focusing on popular data formats found on the target computers hard drive, network shares and removable media. On the outside, these items become considerably skewed as well the filenames undergo scrambling beyond identification, where each one morphs into a random 1. In addition to this, the ransomware concatenates four hexadecimal characters to encrypted data entries. This suffix is unique for every individual extortion scenario, because it matches a computer specific Machine. Guid registry value. As a result, a sample document will turn into a gibberish string like LQp. Hq. 5a. Nr. J. 3f. Obviously, the user is unable to open any of those. Indicators of Cerber ransomware compromise on infected computers desktop. When the Cerber virus is installed, the first thing it does is determine the country that the machine is located in. If its in a country that matches the infections hard coded blacklist mostly composed of Eastern European states, then no further action is taken. Otherwise, the targeted system gets configured to go through several reboots so that the malicious code takes effect. To this end, the ransomware displays a number of rogue system notifications which, once closed manually, trigger a forcible restart of the PC. The next phase is encryption proper. The malware disregards objects in several directories, including Program Files, Program. Data, Windows, Drivers, and App. Brand Guru Marathi Pdf. DataLocal. In the meanwhile, it encodes everything found during the HDD and network drives scan with the above mentioned symmetric Advanced Encryption Standard. Cerber then adds ransom instructions to the desktop as well as each folder that got hit. The original variant of the perpetrating program would drop the following walkthroughs DECRYPT MY FILES. DECRYPT MY FILES. DECRYPT MY FILES. The latest edition of this Trojan called CRBR Encryptor, which was discovered in July 2. READTHISrandom. READTHISrandom. An additional JPEG version of ransom notes straightforwardly replaces the original desktop wallpaper to put additional pressure on the infected person. Cerber ransomware makes a mess of victims files and drops several ransom notes. According to these notes, the victim needs to navigate to a Tor page titled Cerber Decryptor and use it to send 0. Bitcoin about 1,1. The page also displays a countdown timer to add some urgency to the mix so that the plagued user submits the cryptocurrency within five days, or else the sum will become 1 Bitcoin. The darknet service in question allows deciphering one file free of charge, but thats certainly cold comfort given the big picture of the quandary. An unordinary hallmark sign of this infection is that its equipped with a VBScript based text to speech component that recurrently plays an audio message explaining what happened to the data and how to get it back. The message goes, Your documents, photos, databases and other important files have been encrypted. This is, obviously, a clever scare tactic that makes the attack an awful nuisance, not just a commonplace cipher backed predicament. Notwithstanding the whole sophistication of Cerber ransomware, some techniques can help victims restore their files without having to pay the fee or somehow crack the strong encryption. Cerber ransomware automated removal and data recovery. Owing to an up to date database of malware signatures and intelligent behavioral detection, the recommended software can quickly locate the infection, eradicate it and remediate all harmful changes. So go ahead and do the following 1. Download and install the antimalware tool. Open the solution and have it check your PC for PUPs and other types of malicious software by clicking the Start Computer Scan button. Rest assured the scan report will list all items that may harm your operating system. Select the detected entries and click Fix Threats to get the troubleshooting completed. Data recovery toolkit to the rescue. Some strains of ransomware delete the original files after the encryption routine has been completed. As hostile as this activity appears, it can play into your hands. There are applications designed to revive the information that was obliterated because of malfunctioning hardware or due to accidental removal. The tool called Data Recovery Pro by Pareto. Logic features this type of capability therefore it can be applied in ransom attack scenarios to at least get the most important files back. So download and install the program, run a scan and let it do its job. Cerber ransomware manual removal. Some ransomware strains terminate themselves after completing the encryption job on a computer, but some dont. Furthermore, the Cerber virus may prevent victims from using popular antimalware tools in order to stay on board for as long as possible. Under the circumstances, it may be necessary to utilize the Safe Mode with Networking or System Restore functionality. Boot into Safe Mode with Networking. Jay Jay Earns His Wings Software Inc on this page. The method to do it depends on the version of the infected operating system. Follow the instructions below for your OS build. In Safe Mode, the ransom Trojan wont keep security software from running or otherwise thwart troubleshooting. Solaris 10 Kernel Patch Level. Open your preferred web browser, download and install an antimalware tool of choice and start a full system scan. Have all the detected ransomware components removed in a hassle free way. System Restore enables Windows users to roll back all changes made to the OS since the latest restore point creation time. This feature can help eliminate the most persistent ransomware. Before going this route, though, make sure System Restore had been enabled prior to the breach, otherwise the method will be inefficient. Be advised that even after the ransomware is removed, files will still be encrypted and inaccessible. The malicious code cleanup part, however, is important because it keeps a relapse of the infection from occurring further on and eliminates all opportunistic malware. Not only are you a lucky person in case youve been backing up your most important files, but youre also a wise and prudent user. This isnt necessarily a resource heavy activity these days in fact, some providers of online services are allocating a sufficient size of cloud storage space for free so that every customer can easily upload their critical data without paying a penny. Having removed Cerber ransomware, therefore, all you have to do is download your stuff from the remote server or transfer it all from an external piece of hardware if thats the case. A positive upshot of using this technique depends on whether or not the ransomware has erased the Volume Shadow Copies of the files on your PC. This is a Windows feature that automatically makes and keeps the backups of data elements on the hard drive as long as System Restore is enabled.